System Logs
The system logs are accessible via the sidebar, menu point "Logs".
Each performed action is logged and is shown on this page. The page is divided into three tabs:
- User Logs - Actions performed by users, for example, an operating system reinstallation.
- System Logs - Actions performed by the system, for example, PXE data synchronization.
- Remote Agents - Actions performed by remote agents, for example, DHCP configuration rewrites.
Note: Some irrelevant actions are not logged. For example, API queries to the CSRF API, or the get power status API. Otherwise, the database would become too large.
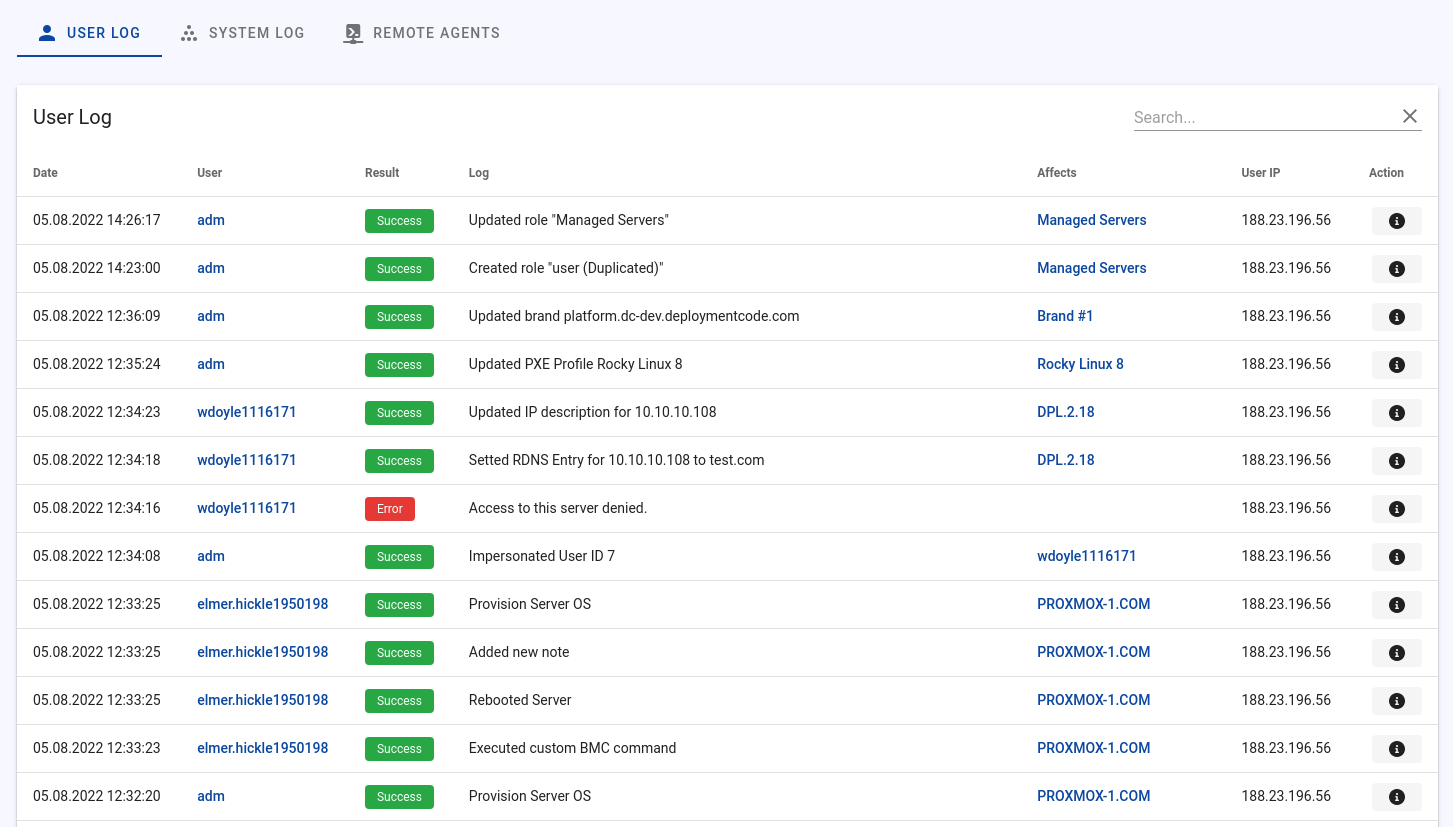
User Logs
The User Logs show information about the actions performed by users. The following data is recorded:
- Date
- Username
- Result (success / error)
- User IP
- Description
- Affected item (e.g. server X)
- API endpoint
- Request method (POST, GET, DELETE, PUT, PATCH)
- Loglevel (success, warning, error)
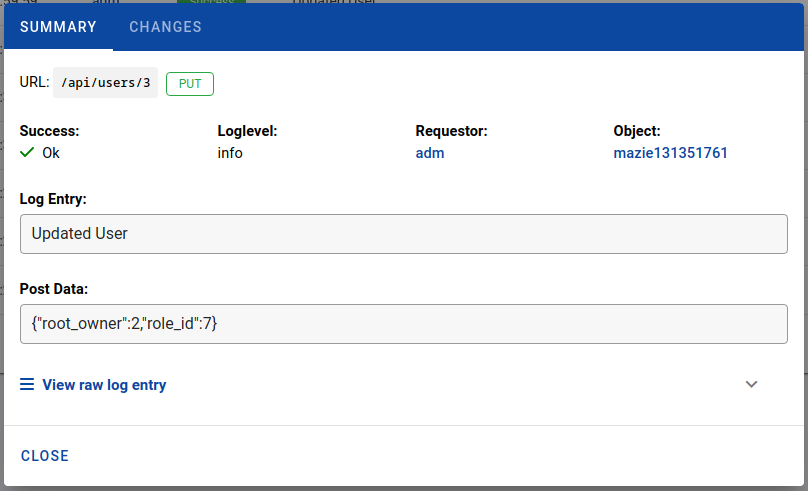
- Request data (full HTTP request body)
- Model changes (Data before and after)
- Request source (API / Web)
Through the detailed log, you can easily determine who made which changes or executed which actions.
In addition to these logs, an per-user API log is available where you can look up which HTTP requests the user has sent to Tenantos. Since the Tenantos web interface is also API based, you will find all requests in the user API request log, not only requests made via an API key.
Accessible by users
If the account has the required permissions (yes by default), non-administrators can also view the logs. Of course, only entries that the user is allowed to see are displayed. Entries for other servers or actions that an administrator has performed on his servers are not shown.
System Logs
The system logs give you insight into what happens through automatic background tasks in Tenantos. Examples would be:
- Orphan files deletion (ISO, PXE)
- Automated hardware inventory update (External providers)
Usually, these logs are not relevant and are only needed if an error occurs.
Remote Agent Logs
The remote agent logs contain information about executions on remote agents. Examples would be:
- Rewrite DHCP configuration.
- Installation of new remote agents.
As with the system logs, the logs are usually not worthy of attention and are only interesting in the case of problems.